
Email measures for organizations
February 15, 2024
The evolution of email: from the past to the present and future
March 13, 2024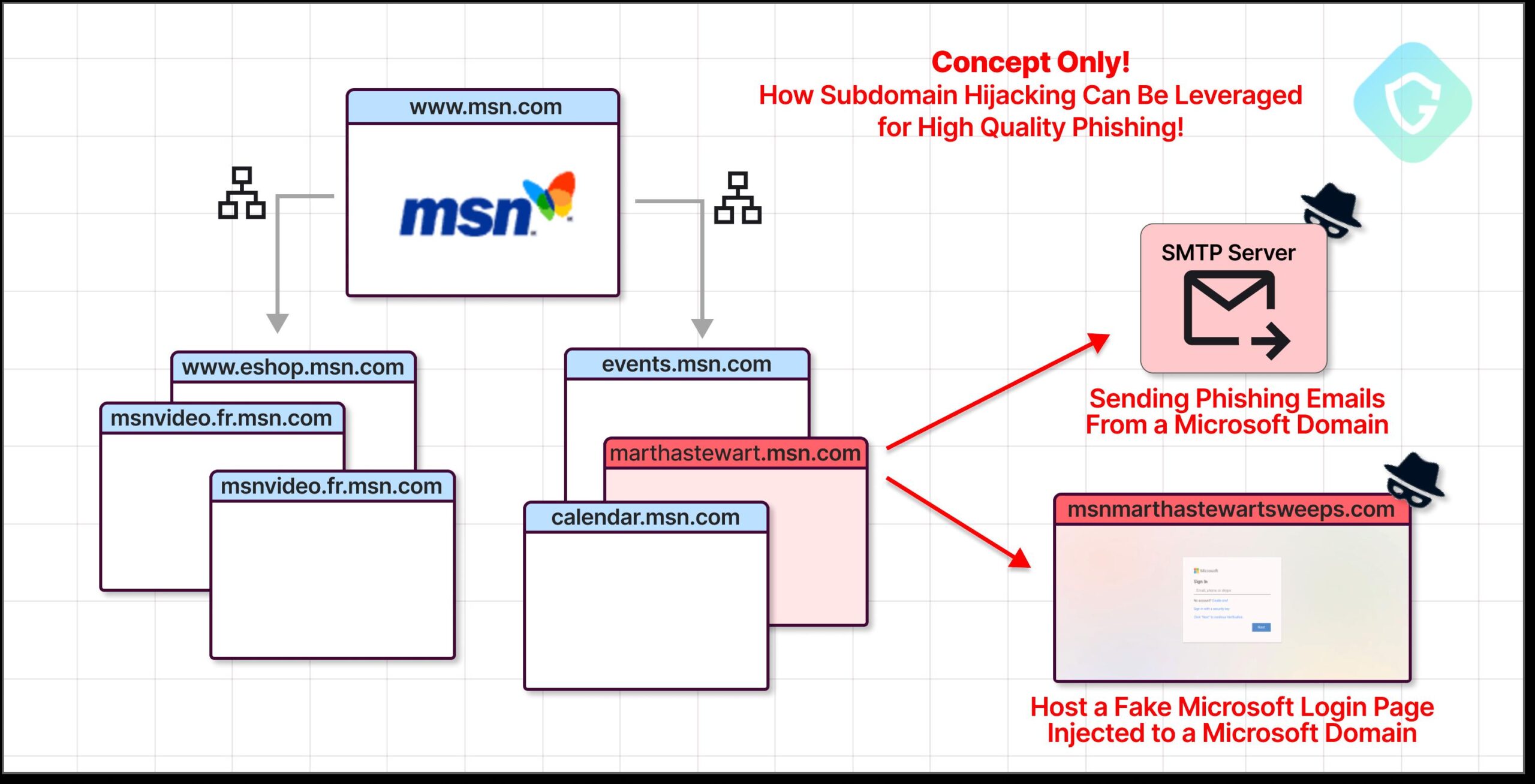
SPF, DKIM, DMARC – insufficient defense. "ResurrecAds", raising significant concerns.
Guardio Labs has revealed that there are more than 8,000 subdomains used by well-known brands and organizations such as MSN, VMware, McAfee, The Economist, Cornell University, CBS, Marvel, eBay, and others. They are sending over a million spam, phishing, or malicious emails per day by faking it in order to exploit the trustworthiness of the security verification system.
These domains belong to trusted companies, giving them the benefit of being able to bypass spam filters and, in some cases, take advantage of SPF and DKIM configurations that tell secure email gateways that these emails are legit and not spam. Using the techniques
CNAME-takeover and SPF-Takeover.
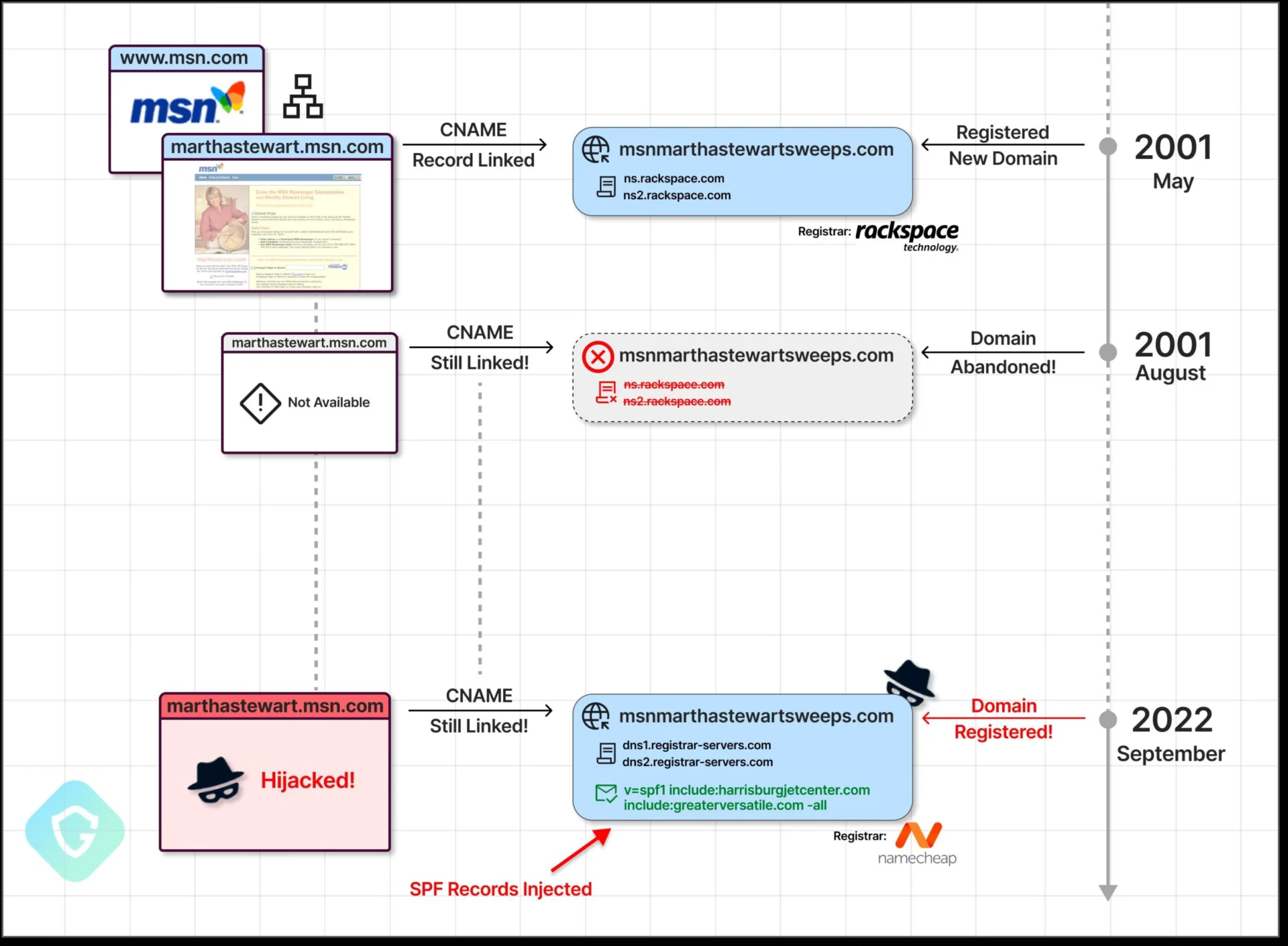
CNAME-takeover
It is a technique used by malicious actors to gain control over domains or subdomains that are inactive or expired. By exploiting a vulnerability in DNS settings that contain references (CNAME records) that point to unused services or hosts.
The attacker performs a CNAME takeover. They can do this by registering inactive or expired domains or by accessing their DNS settings to change the CNAME record to point to an IP address or service they can control. Once the CNAME takeover is complete, attackers can use these domains or subdomains to display web pages, create fake pages, or use them in various attacks.
For system administrators, monitoring and controlling CNAME records is important to protect them, prevent CNAME-takeover, and maintain the security of your organization's domains or subdomains. The security associated with DNS management is therefore especially important.
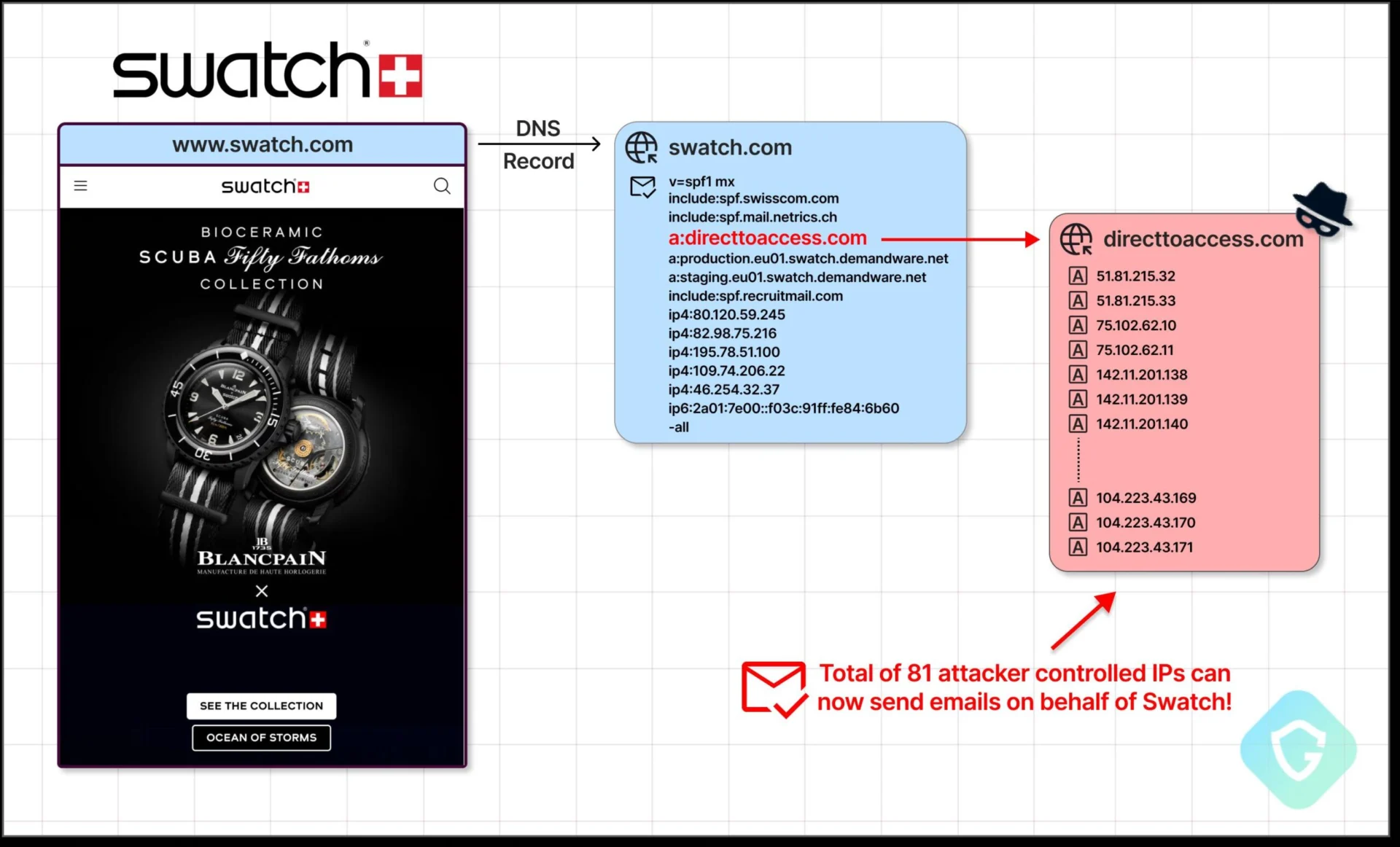
SPF-Takeover
It is a technique used by malicious actors to control the SPF (Sender Policy Framework) settings of unused domains or subdomains, or expired domains. SPF is a technique used to prevent email spoofing, but when attacked with SPF-Takeover, an attacker can access these domains' DNS settings to change the SPF record.
When a domain or subdomain is attacked with SPF-Takeover, the attacker can register inactive or expired domains or even access the DNS settings to change the SPF record for sending emails. This can lead to email spoofing or sending emails with altered SPF records, which can mislead the recipient into believing there is a valid SPF record, causing the system to log in incorrectly. It can also result in a misrepresentation of identity, which can be dangerous.
For administrators, monitoring and controlling SPF record settings is essential to prevent SPF-Takeover and maintain the security of an organization's domains or subdomains.

Researchers from Guardio Labs, Naty Tal and Oleg Saytsev, report that this operation has been in place since 2022. In addition, Guardio Labs has developed a checker "SubdoMailing" - a website designed to allow domain owners to verify and protect themselves from widespread threats. This report not only highlights the seriousness of the problem, but it also motivates the decision to increase the security level of the domain to prevent future attacks.
Source: Guardio Labs

