QR-Code Phishing email
February 5, 2024
Changing email provider
February 11, 2024
Phishing attacks
Phishing statistics showing the % of company departments affected by malicious
According to recent reports, phishing attacks target the following company departments:
- Accounting department (38%)
- Because it contains sensitive financial information
- Often tricked into transferring money illegally
- IT department (22%)
- Because they have access to various systems of the company
- They are often tricked into installing malware.
- Management department (16%)
- It is a high value target.
- They are often tricked into revealing secret information.
- HR department (12%)
- Collect personal information of employees
- They are often tricked into revealing personal information.
- Other Departments (12%)
- Such as sales department, marketing department, customer relations department
Note
- These statistics may vary. It depends on the industry, type of business, and size of the company.

Phishing attack on HR department
Cause of attack
The reason why phishing emails target departments or departments related to human resources (HR) or accounting is due to a number of factors in favor of bad actors. These may include
- Identity Theft : Hackers attack HR departments to obtain employee identities. To be used in disguise or in understanding the company's systems.
- Vulnerable link attack: This attack sometimes sends emails containing vulnerable links. To make the employee click and make the attack more severe.
- Requesting Financial Information (Financial Information Scam): Hackers may copy emails from the accounting department. To request financial information or inquire about transferring money.
- Virtual Creation (Business Email Compromise): This attack can occur by impersonating an email from an organization facilitator, such as an executive, and then using this trick to attack the accounting department or causes incorrect money transfers.
- Sensitive HR Resources: Attacks focused on HR departments may focus on requesting sensitive information about employees, such as employment information, work records. , or personal financial information.
Understanding the nature of this attack can help organizations more effectively plan and defend against malicious phishing attacks.
Attacks on the HR department
HR departments are often hit by phishing attacks for the following main reasons:
- Personal Information: HR departments collect a lot of personal information about employees, such as names, addresses, contact information, ID numbers. Salary information, health information, etc. All of this information is valuable to cybercriminals. to be used in disguise
- System Access: HR employees often have access to important company systems such as the payroll system, benefits system, leave system, etc. Cybercriminals can use this information to gain access to the system and steal sensitive information.
- Scam: Cybercriminals can impersonate HR employees to trick employees into revealing personal information or transferring money.
Attacks on the accounting department
Accounting Department Phishing is often attacked for the following main reasons:
- Fund Transfer: The accounting department is responsible for transferring company funds. Cybercriminals can use phishing to trick accounting employees into transferring money to their accounts.
- Financial Information Scam: The accounting department collects company financial information such as bank information, credit card information. Invoice data, etc. All of this information is valuable to cybercriminals. To copy an email from the accounting department
- Embezzlement: Cybercriminals can use Phishing to trick accounting staff into embezzling company funds.
Phishing example
Examples of Phishing that focus on attacking HR departments or accounting departments:
- Fake Emails: Cybercriminals send fake emails pretending to be from HR or accounting departments. These emails may prompt employees to update their personal information. Click the link to download the document. or transfer money to another account
- Fake Websites: Cybercriminals create fake websites that pretend to be company websites. Employees may accidentally enter personal or financial information on these websites.
- Fake phone calls: Cybercriminals call employees and pretend to be from HR or accounting. They may trick employees into revealing personal information or transferring money.
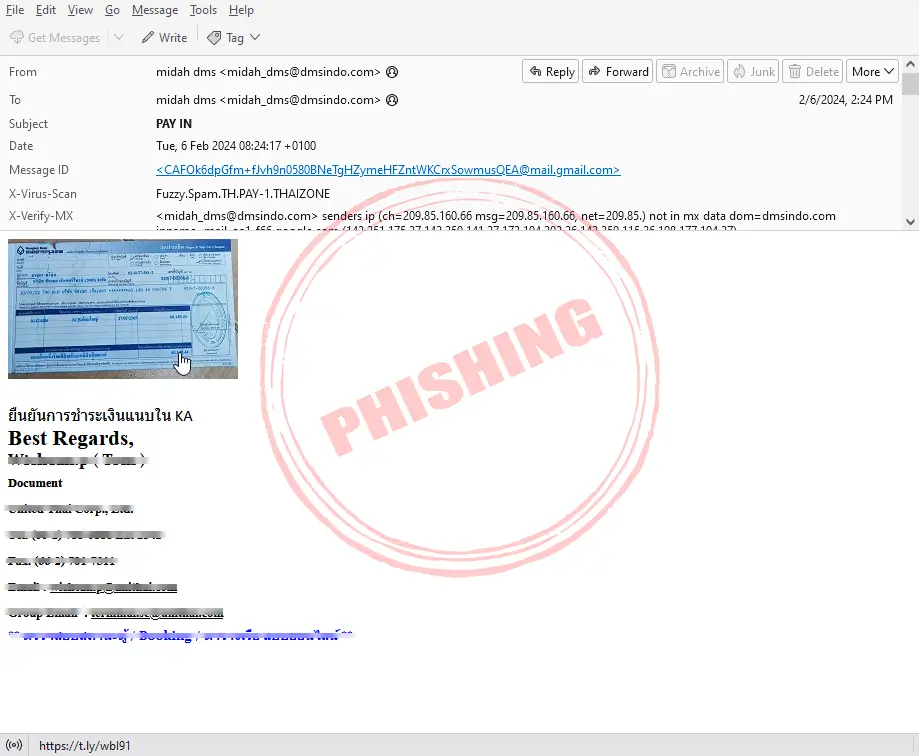
Phishing examples from real systems
From the sample, it was found that a copy of the money transfer is attached to make it look real, and links to websites created by disguising real website pages are inserted to deceive information such as the username and password of the victim. If the victim is not careful, they may fill out various information and send it to the wrong person without realizing it.
In detecting phishing emails like this, machine learning, or a form of AI, plays a key role in spam detection, being more effective than traditional methods such as keyword filters. Because the machine learning system can intelligently learn spam patterns and behaviors.
Our email system has been developed and improved to better understand email behavior that is spam in various forms. We also analyze the information that appears in various parts of the email. We have created our own virus signature database to detect and prevent viruses, phishing, and scams that come with emails effectively. This makes the system faster and better at protecting against threats.
How to prevent Phishing:
- Employee Training: Educate employees about cyber threats and methods of phishing attacks.
- Use protection technology: Install Anti-virus and Anti-malware software.
- Two-factor authentication (2FA): Add a layer of security with 2FA.
- Check website URL: Make sure the website URL is correct before entering information.
- Beware of phone phishing: Beware of people calling claiming to be representatives of the company.
In an era where technology plays a key role in business operations, being vigilant against phishing attacks is extremely important. Focus on the HR or accounting department It is a method used by bad actors to steal valuable information and create confusion in organizations. Planning and creating an effective response is essential to protect the security of your company's data and resources.